What is Canvas Fingerprinting and How to Bypass it
Advanced Data Extraction Specialist
Canvas fingerprinting is a type of online tracking that captures unique information about a user’s device without relying on traditional methods, like cookies. This approach involves creating a "fingerprint" of a user's device by instructing the browser to draw hidden graphics on an HTML5 canvas element, which then records subtle variations unique to that device's hardware and software. These subtle differences are enough to identify and track users across different websites. While the technique is powerful for advertisers and analytics providers, it also raises significant privacy concerns. This article explores how canvas fingerprinting works, its applications, and how users can bypass it.
What is Canvas Fingerprinting?
Canvas fingerprinting works by using the HTML5 <canvas> element to render an image or text, then analyzing how that content is drawn. This image is influenced by various device and browser-specific factors, such as graphics card, operating system, browser version, and installed fonts. When a user accesses a site that employs canvas fingerprinting, the site can generate and save a unique hash code based on the rendering output of the canvas. This hash serves as a digital fingerprint, which remains consistent even when cookies or other traditional tracking methods are blocked or deleted.
Unlike cookies, canvas fingerprints are more challenging for users to detect or control, as they don’t leave any files on a user’s device. This makes canvas fingerprinting particularly effective for “stateless” tracking, as it does not depend on storing data on the client side.
Why is Canvas Fingerprinting Used?
Canvas fingerprinting is popular for several reasons:
- Ad Targeting: It allows advertisers to track users across different websites and build detailed profiles, even when users employ privacy measures such as clearing cookies or using incognito mode.
- Security and Fraud Detection: Some companies use fingerprinting to prevent fraud by verifying that a device is consistent across multiple sessions.
- Analytics: Websites and platforms can use fingerprinting to collect user behavior data, which helps improve the user experience and optimize content.
How Does Canvas Fingerprinting Work?
Canvas fingerprinting is a technique used to track users by generating a unique fingerprint based on a device's graphical rendering capabilities. When a user visits a webpage with this technology, a JavaScript script is executed to draw a specific image or text on an HTML5 <canvas> element. This image is rendered with random variations, making it unique to the user's device due to differences in the operating system, GPU, browser, and other environmental factors.
Step-by-Step Breakdown:
-
Requesting Canvas Data: Upon visiting a page using canvas fingerprinting, the site runs JavaScript that instructs the browser to draw an image or text on the canvas element.
-
Rendering Specifics: The browser's rendering is influenced by the device’s hardware (e.g., GPU), installed fonts, and software, which results in slight variations in the image or text. For example, modern devices may apply anti-aliasing, hinting, or other techniques that change the visual output.
-
Hash Generation: After the content is rendered, the site captures the image or text and generates a unique hash based on that rendering. This hash serves as the user's fingerprint.
-
Tracking Across Sites: With the fingerprint stored, websites can track users across different sessions and even different sites, without relying on cookies.
Example of Canvas Fingerprinting
Here’s a basic JavaScript example of how canvas fingerprinting might work:
javascript
var canvas = document.createElement('canvas');
var ctx = canvas.getContext('2d');
ctx.font = '16px Arial';
ctx.fillText('Hello, world!', 10, 50);
var imageData = canvas.toDataURL();
console.log(imageData);In this example, the text "Hello, world!" is drawn on the canvas, and the toDataURL() method produces a Base64-encoded string representing the image. This string is unique to the user's device because it depends on factors like the operating system, the browser’s rendering engine, and the device’s GPU.
Even if the content looks the same across different devices, the rendering might differ subtly, like different smoothing techniques, fonts, or pixel renderings. These differences generate unique fingerprints for each device.
Tools for Examining Fingerprints
To examine a user’s fingerprint, you can use tools like BrowserLeaks:
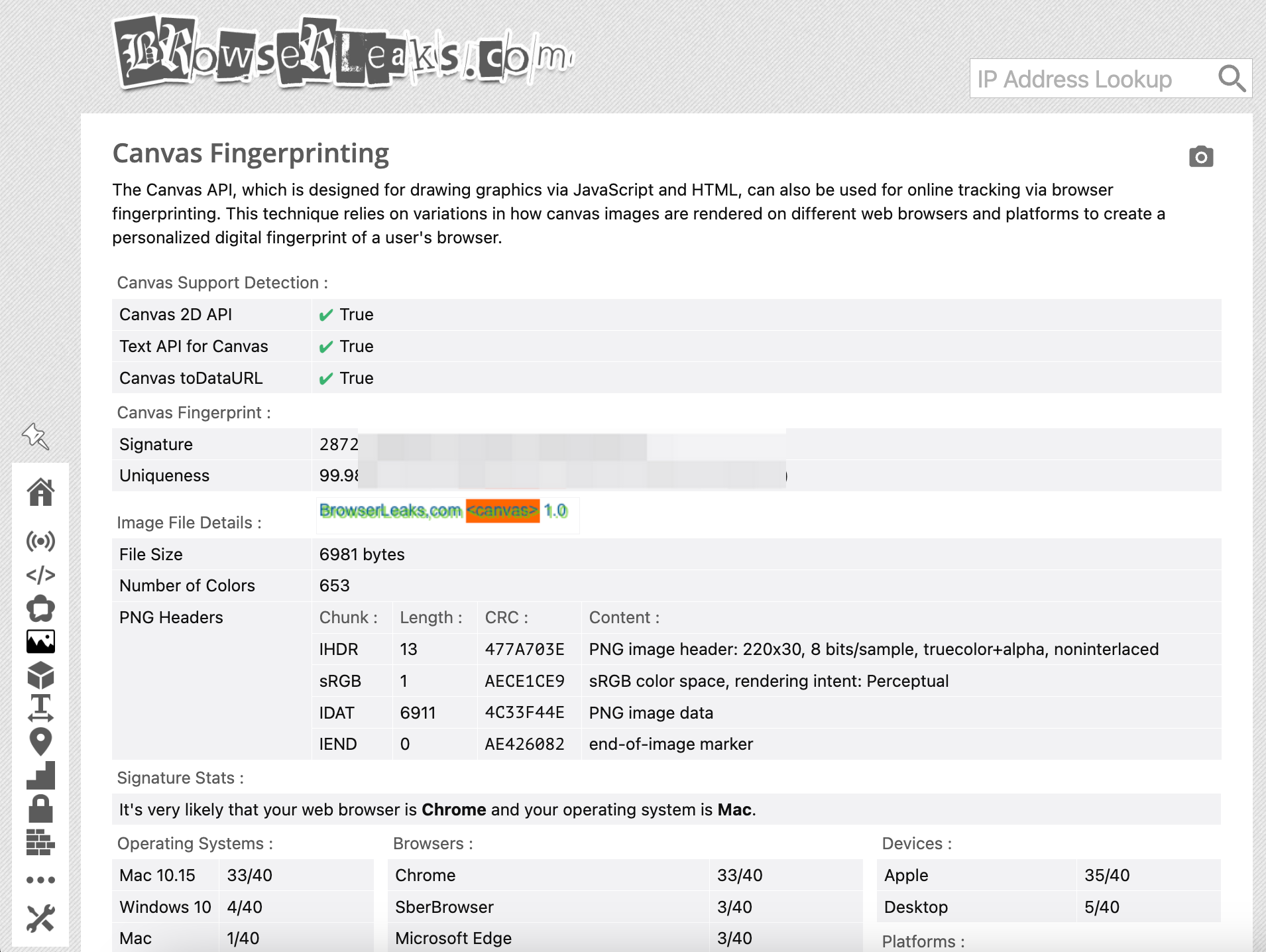
The hash value of the generated image is a key part of the fingerprinting process. Understanding how this hash is generated is essential for bypassing canvas fingerprinting.
How Hashing Works in Canvas Fingerprinting
Since the image data produced by canvas fingerprinting can be large, hashing is used to convert it into a shorter, fixed-length string, known as a hash. Hashing functions ensure that the same input always results in the same output.
For instance, if we input the phrase “unique fingerprint” into an SHA-256 hash function, the output will be:
d2d2d2c6e2f2e4fa2d54c7c16ad01a3177c8d24138d2872b577a229ec0b963f0
If we change the input slightly, for example, by changing the "e" in "fingerprint" to "a", the hash will change to:
3a4e7d8f2d25481a9d2d7a03c2f5fe6d813a67c4c4ea8b063f35e2b202ee5e4d
This demonstrates how even minor changes in the input, such as altering the characters or system attributes, can result in entirely different hashes. This characteristic is essential when bypassing canvas fingerprinting because slight differences can invalidate a previously generated fingerprint, making it more difficult to track users across different sessions or devices.
Privacy Concerns with Canvas Fingerprinting
Canvas fingerprinting is a source of significant privacy concerns as it tracks users without their knowledge or explicit consent. The user cannot easily control or detect canvas fingerprinting because it relies on the browser's rendering engine and does not require permission. Additionally, unlike cookies that users can delete, fingerprints are harder to erase, creating a persistent identifier across browsing sessions and websites. This lack of transparency has led to debates around privacy and data protection, especially under regulations like GDPR, which require user consent for tracking.
How to Bypass Canvas Fingerprinting
Bypassing canvas fingerprinting can be challenging since it relies on rendering subtle, device-specific details to create a unique identifier. However, there are several strategies that can help mask or obscure these details, making it more difficult for websites to generate a reliable fingerprint. The goal is to modify or manipulate the way the canvas element works in order to return a consistent or unidentifiable result, disrupting the tracking process.
Manipulating the Canvas Rendering Process
A common way to bypass canvas fingerprinting is by directly modifying the rendering output. Since canvas fingerprinting relies on the unique rendering of graphics or text, a method of altering the result can be effective. For example, one approach is to intervene in the getImageData() function of the <canvas> element to force it to return a uniform or random image. This can be done using JavaScript to override the method:
javascript
HTMLCanvasElement.prototype.getContext = (function(original) {
return function(type) {
var context = original.call(this, type);
var originalGetImageData = context.getImageData;
context.getImageData = function(x, y, width, height) {
return {
data: new Array(width * height * 4).fill(255) // Returning a uniform image (blank)
};
};
return context;
};
})(HTMLCanvasElement.prototype.getContext);In this code, we override the getContext method, which is used to access the canvas's context and drawing functions. By altering the getImageData function, we make it return a blank, uniform image every time it is called. This prevents websites from obtaining the unique canvas data that they need for fingerprinting. While this technique is not foolproof, it can significantly reduce the effectiveness of canvas fingerprinting.
Using Privacy-Focused Browsers and Extensions
Another approach is to use privacy-focused browsers like Tor or those with built-in anti-tracking measures. These browsers often include features that disrupt fingerprinting techniques, including canvas fingerprinting. For example, the Tor browser implements a number of anti-fingerprinting measures, which can prevent consistent canvas data from being captured. The goal is to make every user appear the same across different websites, making it much more difficult for websites to track them individually.
For users who are not comfortable using privacy-focused browsers, there are also browser extensions available that can specifically target and block canvas fingerprinting attempts. Extensions such as CanvasBlocker or Privacy Badger can be added to your browser to prevent scripts from capturing your canvas data. These extensions actively block or randomize the canvas image each time it is drawn, helping to obscure your fingerprint and protect your privacy.
Randomizing Canvas Output
A more technical approach involves randomizing the canvas output to ensure that each time the fingerprinting script runs, the generated image is different. By introducing small, random variations in the text, fonts, or other elements being rendered on the canvas, you can make each fingerprint appear unique, even across multiple visits to the same site.
For example, instead of rendering the same text every time, you can use JavaScript to randomly generate different text or images each time the canvas is used. Here's an example of how you could do this:
javascript
var canvas = document.createElement('canvas');
var ctx = canvas.getContext('2d');
var randomText = Math.random().toString(36).substring(7); // Generate random text
ctx.font = '16px Arial';
ctx.fillText(randomText, 10, 50);
var imageData = canvas.toDataURL();
console.log(imageData);By randomly generating the text (randomText), the resulting canvas image will be different each time it is drawn. This makes it much harder for websites to track the user consistently based on their fingerprint, as the output will never be the same on successive page loads.
Combining Methods for Stronger Protection
To effectively bypass canvas fingerprinting, it's often best to combine these methods. For instance, using a privacy-focused browser along with an extension like CanvasBlocker can add multiple layers of protection. This combination can help you ensure that your device is not consistently generating the same fingerprint, even if certain methods of bypassing are not entirely foolproof.
By manipulating the canvas rendering process, using privacy-enhancing browsers and extensions, and randomizing the output, you can effectively combat canvas fingerprinting. While no method guarantees complete anonymity, taking these steps can significantly reduce the chances of being tracked by websites that rely on this technique.
Scraping Solutions: If you’re a developer looking for scraping solutions, using tools like Scrapeless can help bypass fingerprinting challenges. Scrapeless provides a robust framework for data extraction, allowing users to avoid browser-based tracking techniques by handling requests in an efficient, undetectable manner. Try Scrapeless free today for a powerful and simplified scraping experience.
Conclusion
Canvas fingerprinting is an advanced and covert tracking method that captures unique device details to create persistent identifiers, which are valuable for advertising and security. However, it also raises privacy concerns due to its undetectable nature and resilience to traditional tracking controls like cookies. While bypassing canvas fingerprinting entirely can be difficult, using privacy-focused tools, browsers, and techniques can significantly reduce tracking risks. As the demand for online privacy grows, it’s likely we’ll see increased browser support for anti-fingerprinting features, along with regulatory measures to protect user data from such sophisticated tracking technologies.
At Scrapeless, we only access publicly available data while strictly complying with applicable laws, regulations, and website privacy policies. The content in this blog is for demonstration purposes only and does not involve any illegal or infringing activities. We make no guarantees and disclaim all liability for the use of information from this blog or third-party links. Before engaging in any scraping activities, consult your legal advisor and review the target website's terms of service or obtain the necessary permissions.



